- Application Services
- Next-Gen App Development
- Mobile Application Development
- Modernization
-
-
- Integration ServicesGet seamless integration of various 3rd party services or existing systems for smooth operations of your mobile apps
- Cross PlatformsExcellent user experience and functionality of native apps with multi-platform compatibility
- Legacy System Modernization ServicesLegacy system modernization empowers organizations so that they can work more efficiently and intelligently.
-
-
- DevOps
- Software Testing
-
-
- AI Enabled TestingLeverage AI for testing the quality of your software products
- Functional TestingAutomated Functional Testing for improved quality & faster go-to-market
- STQC CertificationQuality, Excellence, and Innovation – The Hallmarks of Suma Soft
- Performance TestingEliminate performance bottlenecks of business-critical apps to run under expected, peak loads
-
- Scriptless Automation SolutionsFast, reliable, and easy testing with our “Ready-to-Deploy” automation framework
- Devops TestingOptimize testing in CI/CD pipelines for greater agility, efficiency, and quality
- AA CertificationEmpaneled Certifier for Account Aggregator (AA) Ecosystem
- ABDM Ecosystem Sandbox Exit ProcessWe Certify Your API for ABDM Sandbox Integration And Exit Process
-
-
- AI/ML Services
- AI/ML ServicesStay ahead of the curve with our advanced AI/ML capabilities
- Data Engineering ServicesDrive data-driven decision-making with our agile and customizable data engineering solutions
- Software Product Engineering ServicesTransform your concepts into market-leading products with our strategic product engineering approach
- VaniePartner with Us for Innovative Web App Solutions!
- Indiastack
- Account AggregatorGet certified using Daksh DEPA Validator to go live on the AA network.
- Ayushman Bharat Digital Mission (ABDM)Get certified using Daksh DEPA Validator to go live on the ABDM network.
- Beckn Protocol ImplementationImplement Beckn protocol to go live on India Stack network.
- ONDC CertificationGet certified using Daksh DEPA Validator to go live on the ONDC network.
- O Rickshaw Pune’s First ONDC Mobility App
- Business Services
- Business Process Management
-
-
- Healthcare BPO ServicesRound the clock coverage for most critical industry
- Logistics BPO & Supply Chain ManagementSmarter supply chains Built for today and ready for tomorrow
- Data Entry ServicesEnsure the accuracy and security of your data with Suma Soft
- Underwriting support servicesStreamline underwriting processes , increase accuracy, reduce risk with expert support services.
- Finance and Accounting ManagementImproving Account Payable and Receivables Through Artificial Intelligence
-
- Logistics BPO ServiceOptimize logistics with efficient operations, reduced costs, and our improved visibility.
- Customer Support ServicesSmart use of technology makes all the difference in CX
- REIT Management ServicesProductivity for You. Transparency for Your Investor
- OCR Outsourcing ServicesAchieve faster, accurate and reliable data capture with OCR outsourcing solutions.
- Claims ManagementState-of-the-art technology to assist in responding to rapidly-evolving claim situations
-
-
- Tech Support
-
-
- Desktop SupportResponsive, Day-to-Day Tech Assistance
- Network SupportCreate a comprehensive network security strategy for protecting the enterprise end-to-end
- Active Directory SupportMinimize the risk of disrupting critical business apps while optimizing the performance of MS infrastructure
- Microsoft Exchange SupportStay on top of imminent threats to achieve a glitch-free network with rapid Microsoft Exchange support
-
- L1 & L2 SupportOptimize performance with round-the-clock technical support cater to your business goals
- Remote MonitoringKeep your IT systems running smoothly and ensure the stability and security of your IT environment for the workforce
- NOCGet unrivaled NOC services & scale immediately to enhance your bottom-line profitability with 24*7 services
-
-
- Hyperautomation
-
- Cyber Security
-
-
- AssessmentTest your applications and networks to identify & fix vulnerabilities exposing your sensitive assets
- Cloud SecurityIntelligence and expertise providing a new level of cyber-immunity
- Managed SecurityComprehensive security architecture with flexible enforcement for advanced protection
- Digital ForensicsEmpower your organization to access, manage and leverage Digital Data
-
-
- ServiceNow
- ServiceNow Managed ServicesOngoing ServiceNow support and optimization for peak performance.
- ServiceNow Integration ServicesOngoing ServiceNow Integration Services
- ServiceNow Implementation ServicesExpert ServiceNow implementation for customizable business solutions.
- ServiceNow Migration ServiceAchieve seamless platform transitions with smooth ServiceNow migration.
- ServiceNow Consulting ServicesStrategic ServiceNow consulting for optimal platform utilization.
- ServiceNow ITBM ImplementationImplement ITBM for strategic IT planning and execution.
- ServiceNow ITSM Implementation ServicesPlan and streamline IT service management with expert implementation services.
- ServiceNow Chatbot DevelopmentEnhance user experience with intelligent ServiceNow chatbot solutions.
- ServiceNow CSM ImplementationImprove customer service with efficient ServiceNow CSM implementation.
- ServiceNow GRC ImplementationManage governance, risk, and compliance with ServiceNow GRC.
- ServiceNow Security OperationsStrengthen security posture with ServiceNow security operations management.
- ServiceNow IT Operations Management ServicesOptimize Your IT Operations with automated workflows and efficient service delivery.
- ServiceNow HR Service DeliveryEnhance employee experiences with automated HR service management.
- ServiceNow Financial ManagementStreamline financial operations and improve decision-making with ServiceNow.
- ServiceNow Asset Management ServicesControl IT assets, reduce costs, and ensure compliance with ServiceNow Asset Management.
- Project Portfolio Management ServiceNowPrioritize projects and manage resources for successful delivery.
- Resource Management with ServiceNowStreamline resource allocation for project efficiency and success with ServiceNow Resource Management.
- Business Process Management
- Digital
- Cloud
-
-
- Cloud App Development ServicesGet high security, efficient performance, and excellent operations with cloud apps
- Cloud Testing ServicesDelivering highly polished solutions to help you reduce costs and meet deadlines
- Cloud Migration ServicesA secure cloud single sign-on solution that IT, security, and users will surely love
-
- Enterprise Mobility
- CRM
- Microsoft Dynamics 365 ServicesStreamline business processes with superior BI, automation, and key customer insights
- Custom CRM Development ServicesDigitize processes, enhance everyday managerial activities and engage more customers
- Salesforce Consulting ServicesTransform Your Business with Expert Salesforce Guidance – Elevate Performance and Drive Growth!
- Salesforce testing servicesAchieve end-to-end automation for Salesforce testing
- E-Learning
- Collaboration
- Dusmile Platform
- Cloud
- Insights
- Industries
- Industry We Serve
- Banking And FinanceAccelerate your journey with fintech innovation to reshape customer experience
- GovernmentFully-managed environment for Government, Built for security and compliance
- E-CommerceBest-of-breed technologies to enhance CX and increase revenue to maximize business needs
- E-LearningReimaging education – from remote to hybrid learning
- Logistics & DistributionChanging the landscape of supply chain management
- AutomotiveRevolutionizing automotive development for the digital future
- HealthcareDelivering better experiences, better insights, and better care for better health
- ManufacturingLeverage our deep expertise to modernize your manufacturing and industrial technologies and processes.
- Industry We Serve
- About Us
- About Suma Soft
- HistoryDecades of experience and expertise matched with dedicated professionals.
- LeadershipA leadership that drives Suma Soft to meet its overall goals.
- CertificationsOur recognition as a trusted technology company for orchestrating a successful business transformation
- Our PartnersBringing together the best technologies and practices to offer a prosperous digital future
- Annual ReturnSuma Soft’s Yearly Financial Annual Return Report
- About Suma Soft
- Careers
- Contact Us

What is a Thick Client Application?
We use them daily in the form of web browsers, games, desktop music players, messenger programs, video conferencing tools like Zoom, etc. In simple terms, Thick Client Applications are Desktop applications based on the client-server architecture. The other definition of Thick Applications is the CLIENT in the Client-Server Architecture. From Penetration Testing or “Pentesting” perspective, the Thick Client Applications are tested at the client and server end. Thick Client Applications are developed using programming languages like C/C++, .Net, JAVA, & Microsoft Silverlight, etc. Thick Clients are beneficial as they may not depend on a server on the network and yet perform the bulk of the tasks locally. However, they may require to connect with the Central Server occasionally but can work offline too. In a nutshell, the thickness of the client can be equated with the amount of processing that is done at the client side, and since in the case of Thick Client Applications, significant processing happens at the client-side, the phrase “THICK CLIENT”.
There are two types of architectures in Thick Client Applications.
2-Tier Application
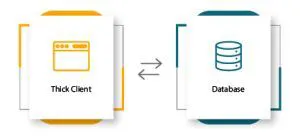
In this kind of Thick Client Application, there are only two entities, a Client and a Server. There is direct communication between the entities [client and server] as there is no intermediate. Usually, the server hosts the data in the database, which the client program can access directly based on a set of protocols. Examples of 2-tier applications are desktop games, music players, Content Management Systems, Customer Relationship Management applications, etc. From a security testing perspective, 2-tier applications offer a larger attack surface for penetration testing. Pentesting 2-tier applications have better success as the client is locally available.
3-Tier Application
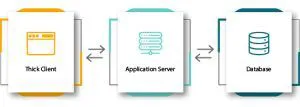
In the case of 3-tier Thick Client Applications, the client cannot communicate directly with the database server. There is a third entity in between – the Application Server. The client passes its request to the Application Server, which communicates with the database and serves the client with the requested data. 3-tier applications are safer than 2-tier Applications as the end-user has no direct access to the database.
Vulnerabilities in Thick Client Applications
The Hybrid Infrastructure on which the Thick Client Application usually resides poses more security challenges than web-based thin clients. To put it in simple terms, the Thick Client Application runs on the user’s system, which might not have adequate security measures in place, and attackers can exploit it. Here is where Thick Client Security, or to put it in a better perspective, Thick Client Penetration Testing, comes into the picture. Thick Client Applications attacks commonly include SQL Injection, Insecure Storage, Denial of Service [DoS], Reverse Engineering, etc.
What is Thick Client Penetration Testing?
Thick Clients are full-blown applications that can function with or without a network. Thick Client Penetration Testing [Pentesting] is a feature of Thick Client Security that scans for weaknesses in the Thick Client Application to improve the security of the Application.
Thick Client Application Testing Methodology

Discovery
Compared to Thin Client Applications, Thick Client Applications are custom-built and hence are relatively complicated. So it becomes prudent to gather all the relevant information about the Application. In this information-gathering phase, you thoroughly understand the following:
- Framework & Architecture
- Understand the technologies like programming language used at the server-side and client-side
- Understanding the functionality of the Application
- Security features of the Application, vulnerabilities, analyzing the user inputs, etc.
UI Elements
Inspect the UI elements of all the user levels. It would be best if you spent considerable time analyzing the permissions and functionalities associated with all the users logging in to the thick client application.
The Programming Language of the Application
Many tools are available that can detect the programming language used to build the Thick Client Application.
Network
This stage of Thick Client Penetration Testing involves tracking data exchange between the client and the server. The client and server can be on the same system or different systems connected through a network. Penetration tester needs to be well versed with the tools used for sniffing network packets. This testing method will provide information related to the network protocols, analyze network traffic, debug network clients, etc. Scrutinizing the traffic between the Thick Client and the server can reveal sensitive information such as API keys, REST API, HTTP/HTTPS endpoints, etc. You would need specialized Proxy tools to intercept the data exchanged between the client undergoing penetration testing and the server.
Proxy Aware Thick Client
In this case, the Application/Software is aware of how to establish a connection with the Proxy Server instead of a Real Server. When pentesting the Proxy-Aware Thick Client, you can use any Proxy tool to intercept the traffic.
Non-Proxy-Aware Thick Client
These clients lack proxy support and there is no way for such a Thick Client to configure proxy options on its own. When analyzing the Non-Proxy Aware Thick Client traffic, you need Burp Suite’s Invisible proxying that connects these types of Thick clients to a Proxy listener.
Client-Side Testing
File Analysis
In this approach the Pentester looks for the sensitive data stored on the local system, this data includes usernames, passwords, API keys, Connection Strings, etc. The improved functionality of client-side web-based applications has also led to an increase in the attack surface.
DLL Hijacking
Dynamic Link Library or DLL files consist of executable code used by other applications. Attackers replace the original DLL files with their own. When the Application runs, the attacker-placed DLL file containing the malicious code gets executed. Thick Client Pentesters employ Process Monitoring Tools that:
- Identify possible DLL hijacking in running processes
- Detects Executable Files that are vulnerable to DLL hijacking.
Reading Configuration Files
In this client-side Thick Application Pentesting method, testers deploy a variety of tools to locate the sensitive information in files and the system registry. In such scenarios, the Pentester may not have any prior knowledge & information about the Thick Client application undergoing testing. Using a decompiler to retrieve the source code of the Application undergoing pentesting. The tools available for testing the security of configuration files perform the following tasks:
- Display Real-time Registry, File-System & Process Activity
- Compare Registry Snapshots before and After System/Software Update
Binary Analysis
In this Thick Client Penetration Testing method Pentesters search the source code of the thick client application for information that includes hardcoded credentials [username/passwords, keys, etc.], API Keys & Endpoints, and Hidden Functions & Comments. The pentesting tools used in Binary Analysis reverse-engineer Binary Files, Decompile, Disassemble & Debug thick client applications.
GUI Weaknesses
In this method, the thick client pentesters check for the GUI vulnerabilities associated with users with different privileges. The pentesting tools used in this method manipulate window objects, such as Text boxes, Buttons, Dropdowns, and Menu bars, in the form. The tools used in this type of Pentesting help you:
- Activate functions that are blocked by the Thick client.
- Manipulate Window Objects
- View & Modify Properties of any Window
Memory Analysis
This method is used to detect the vulnerabilities in 2-tier architecture applications, as Thick-client applications transmit sensitive information to the Application’s memory. This information in the memory can be viewed with the help of specialized Memory Analysis Tools.
OWASP Top 10
- A1 : Injection
- A2 : Broken Authentication
- A3 : Sensitive Data Expose
- A4 : XML External Entities
- A5 : Broken Access Control
- A6 : Security Misconfiguration.
- A7 : Cross Site Scripting.
- A8 : Insecure Deserialization.
- A9 : Using Components with Known Vulnerabilities.
- A10 : Insufficient Logging and Monitoring.
About Author
Saeel Relekar is an Information Security Analyst at – Suma Soft. He is specializes in Thick Client Penetration Testing. Suma Soft is a market leader in Cyber security Services.
Recent Posts
- DevOps in Software Product Engineering: Streamlining Development and Operations September 10, 2024
- Accelerate Your Business with Our Data Engineering Solutions: A Case Study August 20, 2024
- The Role of Cloud Computing in Modern Data Engineering Solutions June 25, 2024
- Why 70% of Enterprises Are Choosing Hybrid Apps and How They Benefit May 24, 2024
- How Building a Native App Can Increase Customer Engagement by 3X May 20, 2024
- What Competitive Advantages Do PWAs Offer Over Traditional Mobile Apps? May 16, 2024
- 5 Must-Have Features for Enterprise-Level iOS Apps May 14, 2024
- 5 Ways to Supercharge Your Android App with AI and Machine Learning May 8, 2024
- Comparing Traditional ETL vs. Modern Data Engineering Approaches April 24, 2024
- Can Outsourcing E-Commerce Customer Service Actually Drive Sales and Brand Loyalty? April 10, 2024
